Elevating Cybersecurity
Harnessing Vast Expertise in Auditing, Cyber Solutions, and Employee Awareness, Collaborative Mastery in On-Premises and Public Cloud, Cost-Effective Visibility Solutions for CIOs and CISOs, and Actionable Intelligence through In-Depth Process, Asset, and Risk Analysis.
API Security
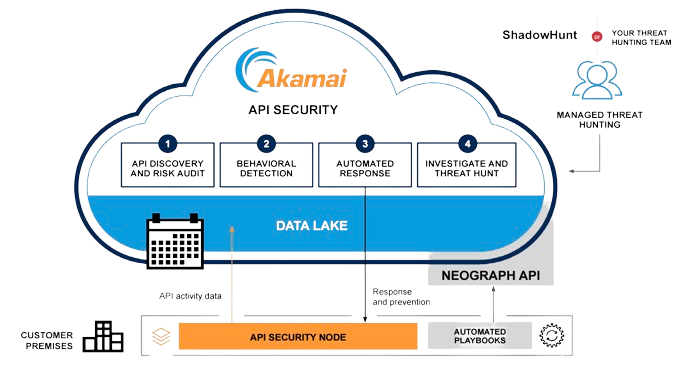
1. Discover
- Continuous API exploration ensures an updated inventory.
- Deep dives into APIs provide thorough risk audits.
2. Test
- Dynamic API scanning identifies security vulnerabilities early.
- Logic vulnerabilities are detected and addressed during software development.
3. Detect
- Big data AI and behavioral analytics detect anomalies within your API estate.
- Alerts are issued to notify anomalies for timely action.
4. Respond
- Written policies trigger automated responses for inline components.
- Actions are pushed to platforms like Jira, texts, or emails based on policy directives.
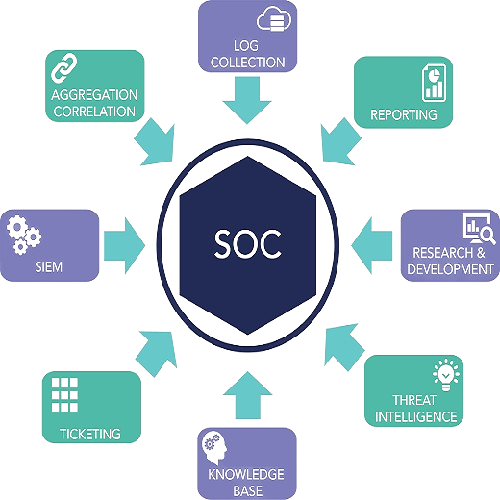
Security Operations Center (SOC)
- Expert SOC Resources
- Real-time Threat Intelligence
- Proactive Threat Hunting
- Swift Incident Response
- Customized Security Solutions
- Comprehensive Endpoint Protection
- OT/ICS Security Expertise
- Continuous Monitoring and Alerting
- Platform Optimization
- Use Case Management
- Managed Detection & Notification
- Security Platform Management
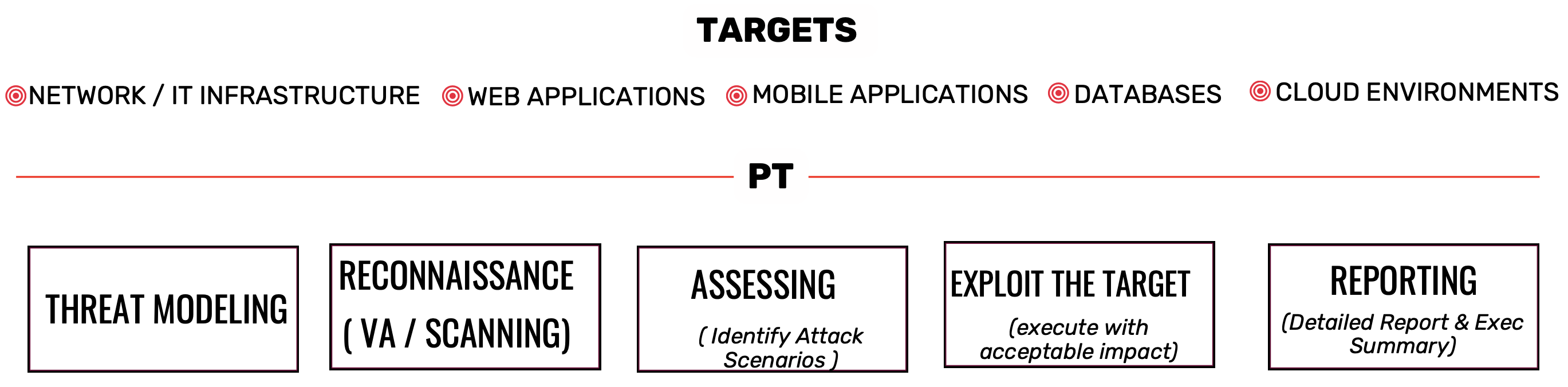
VAPT
Thorough Vulnerability Scanning
- Conduct regular vulnerability scans across your network, applications, and systems to identify potential weaknesses and security gaps. This proactive approach helps in identifying vulnerabilities before they can be exploited by malicious actors.
Comprehensive Penetration Testing
- Perform regular penetration tests to simulate real-world attacks and assess the effectiveness of your security controls. This involves attempting to exploit vulnerabilities in a controlled environment to determine their potential impact and identify any additional security measures needed.
Patch Management
- Implement a robust patch management process to promptly address vulnerabilities identified through VA and PT. This involves regularly applying security patches and updates to software, firmware, and operating systems to mitigate known vulnerabilities and reduce the risk of exploitation.
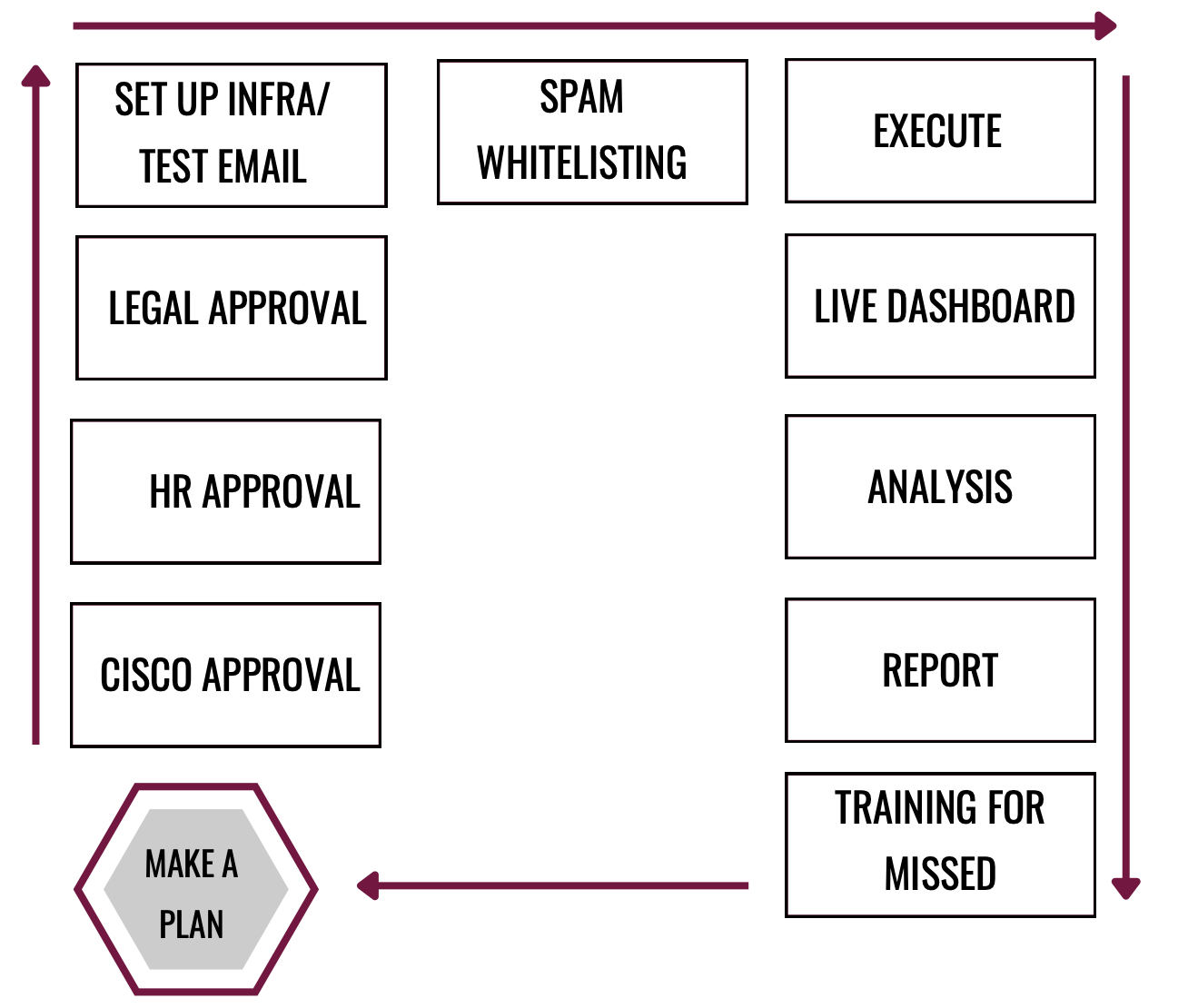
PHISHING SIMULATION
1. Customized Product Positioning.
2. Modifiable Profiles/Execution.
3. Insights and Analytics.
4. Randomizable Realistic Scenarios.
5. New Setup / Infra For Each Delivery.
Planning and Preparation
- Understanding org, profiles, domain, email configuration.
- Test and qualify to ensure max penetration/deceive spam.
Simulation and Execution
- Group, randomize and schedule send the mails.
- Monitor and fine tune.
Analysis and Reporting
- Stagewise report phishing responses.
Training and Awareness
- Instrutor LED training about phishing awareness.
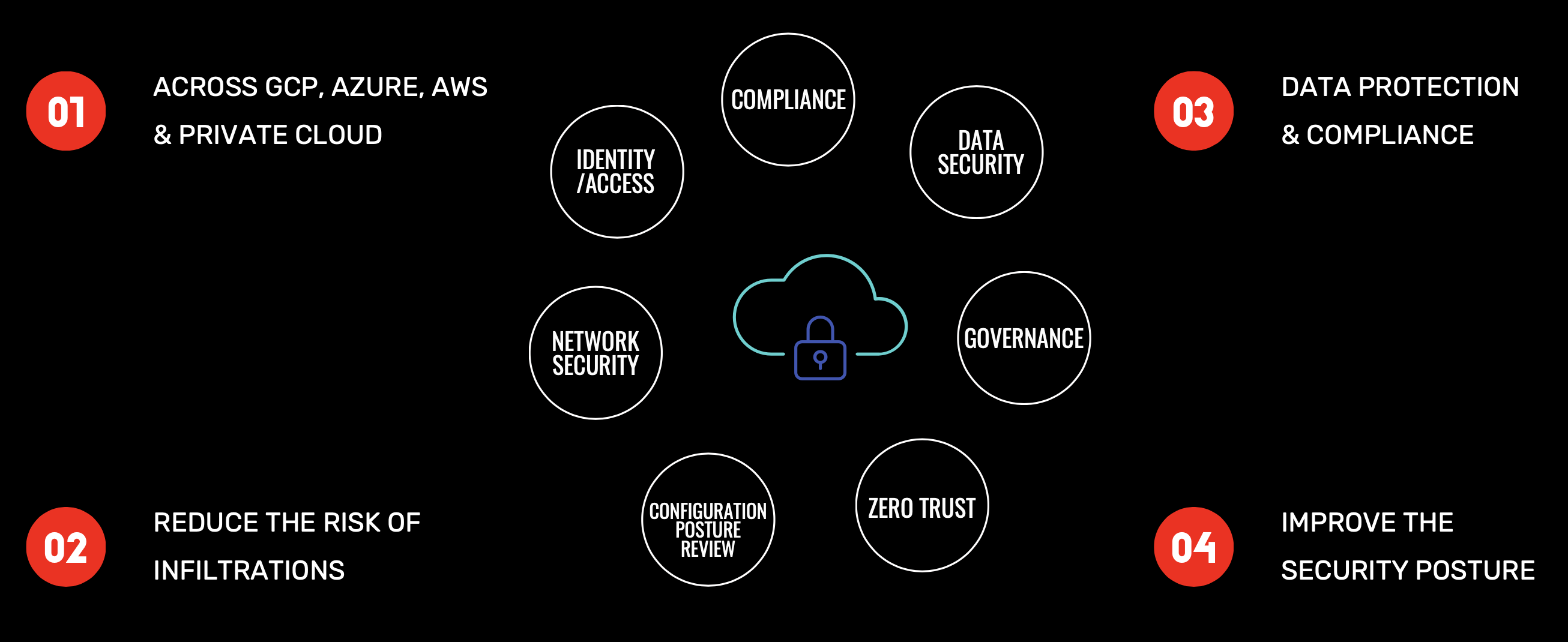
CLOUD SECURITY POSTURE
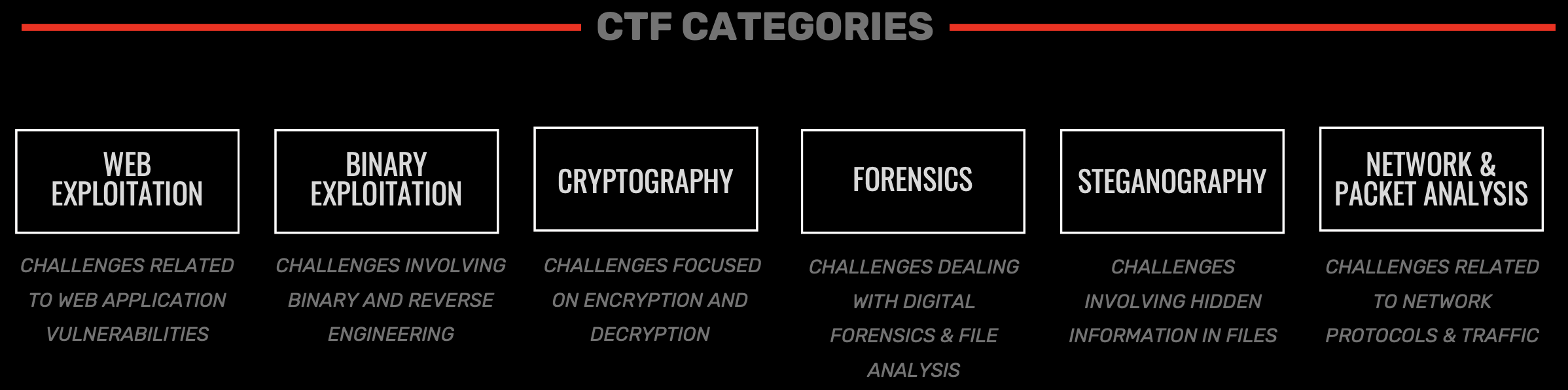
CTF
OSINT
Internet Scans
- Gathering information from publicly accessible websites, forums, social media platforms, & other online sources
Darknet Scans
- Investigating the hidden, anonymized portions of the internet. It explores the anonymous & often illegal portions of the internet, including darknet marketplaces and forums.
Tools Used
Search engines, APIs, Web scraping, Tools, and Data Aggregation platforms.
Specialized darknet search engines, Tor network, and Data monitoring tools.
Information Gathered
Publicly available information, Repos, Leaked information, News article, Social media posts and more.
Information related to illegal activities, Cyber threats and Hidden services.